Developers
API References
Data Subject Request API
Data Subject Request API Version 1 and 2
Data Subject Request API Version 3
Platform API
Key Management
Platform API Overview
Accounts
Apps
Audiences
Calculated Attributes
Data Points
Feeds
Field Transformations
Services
Users
Workspaces
Warehouse Sync API
Warehouse Sync API Overview
Warehouse Sync API Tutorial
Warehouse Sync API Reference
Data Mapping
Warehouse Sync SQL Reference
Warehouse Sync Troubleshooting Guide
ComposeID
Warehouse Sync API v2 Migration
Audit Logs API
Bulk Profile Deletion API Reference
Calculated Attributes Seeding API
Custom Access Roles API
Data Planning API
Group Identity API Reference
Profile API
Pixel Service
Events API
mParticle JSON Schema Reference
IDSync
Client SDKs
AMP
AMP SDK
Android
Initialization
Configuration
Network Security Configuration
Event Tracking
User Attributes
IDSync
Screen Events
Commerce Events
Location Tracking
Media
Kits
Application State and Session Management
Data Privacy Controls
Error Tracking
Opt Out
Push Notifications
WebView Integration
Logger
Preventing Blocked HTTP Traffic with CNAME
Workspace Switching
Linting Data Plans
Troubleshooting the Android SDK
API Reference
Upgrade to Version 5
Cordova
Cordova Plugin
Identity
Direct Url Routing
Direct URL Routing FAQ
Web
Android
iOS
iOS
Workspace Switching
Initialization
Configuration
Event Tracking
User Attributes
IDSync
Screen Tracking
Commerce Events
Location Tracking
Media
Kits
Application State and Session Management
Data Privacy Controls
Error Tracking
Opt Out
Push Notifications
Webview Integration
Upload Frequency
App Extensions
Preventing Blocked HTTP Traffic with CNAME
Linting Data Plans
Troubleshooting iOS SDK
Social Networks
iOS 14 Guide
iOS 15 FAQ
iOS 16 FAQ
iOS 17 FAQ
iOS 18 FAQ
API Reference
Upgrade to Version 7
React Native
Getting Started
Identity
Unity
Upload Frequency
Getting Started
Opt Out
Initialize the SDK
Event Tracking
Commerce Tracking
Error Tracking
Screen Tracking
Identity
Location Tracking
Session Management
Xamarin
Getting Started
Identity
Web
Initialization
Configuration
Content Security Policy
Event Tracking
User Attributes
IDSync
Page View Tracking
Commerce Events
Location Tracking
Media
Kits
Application State and Session Management
Data Privacy Controls
Error Tracking
Opt Out
Custom Logger
Persistence
Native Web Views
Self-Hosting
Multiple Instances
Web SDK via Google Tag Manager
Preventing Blocked HTTP Traffic with CNAME
Facebook Instant Articles
Troubleshooting the Web SDK
Browser Compatibility
Linting Data Plans
API Reference
Upgrade to Version 2 of the SDK
Alexa
Quickstart
iOS Quick Start
Overview
Step 1. Create an input
Step 2. Verify your input
Step 3. Set up your output
Step 4. Create a connection
Step 5. Verify your connection
Step 6. Track events
Step 7. Track user data
Step 8. Create a data plan
Android
Overview
Step 1. Create an input
Step 2. Verify your input
Step 3. Set up your output
Step 4. Create a connection
Step 5. Verify your connection
Step 6. Track events
Step 7. Track user data
Step 8. Create a data plan
Step 9. Test your local app
Python Quick Start
Step 1. Create an input
Step 2. Create an output
Step 3. Verify output
Server SDKs
Node SDK
Go SDK
Python SDK
Ruby SDK
Java SDK
Guides
Partners
Introduction
Outbound Integrations
Outbound Integrations
Firehose Java SDK
Inbound Integrations
Compose ID
Glossary
Migrate from Segment to mParticle
Migrate from Segment to mParticle
Migrate from Segment to Client-side mParticle
Migrate from Segment to Server-side mParticle
Segment-to-mParticle Migration Reference
Data Hosting Locations
Rules Developer Guide
API Credential Management
The Developer's Guided Journey to mParticle
Guides
Composable Audiences
Composable Audiences Overview
User Guide
User Guide Overview
Warehouse Setup
Warehouse Setup Overview
Audience Setup
Frequently Asked Questions
Customer 360
Overview
User Profiles
Overview
User Profiles
Group Identity
Overview
Create and Manage Group Definitions
Calculated Attributes
Calculated Attributes Overview
Using Calculated Attributes
Create with AI Assistance
Calculated Attributes Reference
Predictions
Predictions Overview
What's Changed in the New Predictions UI
View and Manage Predictions
Identity Dashboard (Early Access)
Getting Started
Create an Input
Start capturing data
Connect an Event Output
Create an Audience
Connect an Audience Output
Transform and Enhance Your Data
Platform Guide
The New mParticle Experience
The new mParticle Experience
The Overview Map
Billing
Usage and Billing Report
Observability
Observability Overview
Observability User Guide
Observability Troubleshooting Examples
Observability Span Glossary
Platform Settings
Key Management
Audit Logs
Platform Configuration
Event Forwarding
Event Match Quality Dashboard
Notifications
System Alerts
Trends
Introduction
Data Retention
Data Catalog
Connections
Activity
Data Plans
Live Stream
Filters
Rules
Blocked Data Backfill Guide
Tiered Events
mParticle Users and Roles
Analytics Free Trial
Troubleshooting mParticle
Usage metering for value-based pricing (VBP)
IDSync
IDSync Overview
Use Cases for IDSync
Components of IDSync
Store and Organize User Data
Identify Users
Default IDSync Configuration
Profile Conversion Strategy
Profile Link Strategy
Profile Isolation Strategy
Best Match Strategy
Aliasing
Segmentation
Audiences
Audiences Overview
Create an Audience
Connect an Audience
Manage Audiences
Audience Sharing
Match Boost
FAQ
Inclusive & Exclusive Audiences (Early Access)
Inclusive & Exclusive Audiences Overview
Using Logic Blocks in Audiences
Combining Inclusive and Exclusive Audiences
Inclusive & Exclusive Audiences FAQ
Classic Audiences
Standard Audiences (Legacy)
Predictive Audiences
Predictive Audiences Overview
Using Predictive Audiences
New vs. Classic Experience Comparison
Analytics
Introduction
Core Analytics (Beta)
Setup
Sync and Activate Analytics User Segments in mParticle
User Segment Activation
Welcome Page Announcements
Settings
Project Settings
Roles and Teammates
Organization Settings
Global Project Filters
Portfolio Analytics
Analytics Data Manager
Analytics Data Manager Overview
Events
Event Properties
User Properties
Revenue Mapping
Export Data
UTM Guide
Analyses
Analyses Introduction
Segmentation: Basics
Getting Started
Visualization Options
For Clauses
Date Range and Time Settings
Calculator
Numerical Settings
Segmentation: Advanced
Assisted Analysis
Properties Explorer
Frequency in Segmentation
Trends in Segmentation
Did [not] Perform Clauses
Cumulative vs. Non-Cumulative Analysis in Segmentation
Total Count of vs. Users Who Performed
Save Your Segmentation Analysis
Export Results in Segmentation
Explore Users from Segmentation
Funnels: Basics
Getting Started with Funnels
Group By Settings
Conversion Window
Tracking Properties
Date Range and Time Settings
Visualization Options
Interpreting a Funnel Analysis
Funnels: Advanced
Group By
Filters
Conversion over Time
Conversion Order
Trends
Funnel Direction
Multi-path Funnels
Analyze as Cohort from Funnel
Save a Funnel Analysis
Explore Users from a Funnel
Export Results from a Funnel
Saved Analyses
Manage Analyses in Dashboards
Query Builder
Data Dictionary
Query Builder Overview
Modify Filters With And/Or Clauses
Query-time Sampling
Query Notes
Filter Where Clauses
Event vs. User Properties
Group By Clauses
Annotations
Cross-tool Compatibility
Apply All for Filter Where Clauses
Date Range and Time Settings Overview
User Attributes at Event Time
Understanding the Screen View Event
User Aliasing
Dashboards
Dashboards––Getting Started
Manage Dashboards
Organize Dashboards
Dashboard Filters
Scheduled Reports
Favorites
Time and Interval Settings in Dashboards
Query Notes in Dashboards
Analytics Resources
The Demo Environment
Keyboard Shortcuts
User Segments
Data Privacy Controls
Data Subject Requests
Default Service Limits
Feeds
Cross-Account Audience Sharing
Import Data with CSV Files
Import Data with CSV Files
CSV File Reference
Glossary
Video Index
Analytics (Deprecated)
Identity Providers
Single Sign-On (SSO)
Setup Examples
Introduction
Developer Docs
Introduction
Integrations
Introduction
Rudderstack
Google Tag Manager
Segment
Data Warehouses and Data Lakes
AWS Kinesis (Snowplow)
Advanced Data Warehouse Settings
AWS Redshift (Define Your Own Schema)
AWS S3 Integration (Define Your Own Schema)
AWS S3 (Snowplow Schema)
BigQuery (Snowplow Schema)
BigQuery Firebase Schema
BigQuery (Define Your Own Schema)
GCP BigQuery Export
Snowflake (Snowplow Schema)
Snowplow Schema Overview
Snowflake (Define Your Own Schema)
Developer Basics
Aliasing
Integrations
24i
Event
Aarki
Audience
ABTasty
Audience
AdChemix
Event
Actable
Feed
Adobe Marketing Cloud
Cookie Sync
Server-to-Server Events
Platform SDK Events
AdMedia
Audience
Adobe Audience Manager
Audience
Adobe Campaign Manager
Audience
Adobe Experience Platform
Event
Adobe Target
Audience
AgilOne
Event
Algolia
Event
AdPredictive
Feed
Amazon Advertising
Audience
Amazon Kinesis
Event
Amazon Redshift
Data Warehouse
Amazon S3
Event
Amazon SQS
Event
Amazon SNS
Event
Amobee
Audience
Anodot
Event
Antavo
Feed
Apptentive
Event
Apptimize
Event
Apteligent
Event
Awin
Event
Bidease
Audience
Microsoft Azure Blob Storage
Event
Bing Ads
Event
Bluecore
Event
Bluedot
Feed
Branch S2S Event
Event
Bugsnag
Event
Cadent
Audience
Census
Feed
comScore
Event
Conversant
Event
Crossing Minds
Event
Custom Feed
Custom Feed
Databricks
Data Warehouse
Datadog
Event
Didomi
Event
Eagle Eye
Audience
Edge226
Audience
Epsilon
Event
Emarsys
Audience
Everflow
Audience
Facebook Offline Conversions
Event
Google Analytics for Firebase
Event
Flybits
Event
Flurry
Event
FreeWheel Data Suite
Audience
ForeSee
Event
Google Ad Manager
Audience
Friendbuy
Event
Google Analytics
Event
Google Analytics 4
Event
Google BigQuery
Audience
Data Warehouse
Google Enhanced Conversions
Event
Google Marketing Platform
Audience
Cookie Sync
Event
Google Marketing Platform Offline Conversions
Event
Google Pub/Sub
Event
Google Tag Manager
Event
Heap
Event
Herow
Feed
Ibotta
Event
Hightouch
Feed
ID5
Kit
Hyperlocology
Event
Impact
Event
InMarket
Audience
Inspectlet
Event
Intercom
Event
ironSource
Audience
Kafka
Event
Kissmetrics
Event
Kubit
Event
LaunchDarkly
Feed
LifeStreet
Audience
LiveLike
Event
Liveramp
Audience
MadHive
Audience
Localytics
Event
mAdme Technologies
Event
Marigold
Audience
MediaMath
Audience
Mediasmart
Audience
Microsoft Ads
Microsoft Ads Audience Integration
Microsoft Azure Event Hubs
Event
Mintegral
Audience
Monetate
Event
Movable Ink
Event
Movable Ink - V2
Event
Multiplied
Event
Nami ML
Feed
Nanigans
Event
NCR Aloha
Event
Neura
Event
OneTrust
Event
Oracle BlueKai
Event
Paytronix
Feed
Persona.ly
Audience
Personify XP
Event
Plarin
Event
Primer
Event
Qualtrics
Event
Quantcast
Event
Rakuten
Event
RevenueCat
Feed
Reveal Mobile
Event
Salesforce Mobile Push
Event
Scalarr
Event
Shopify
Custom Pixel
Feed
Singular-DEPRECATED
Event
Skyhook
Event
SimpleReach
Event
Slack
Event
Smadex
Audience
SmarterHQ
Event
Snapchat Conversions
Event
Snowflake
Data Warehouse
Snowplow
Event
Splunk MINT
Event
StartApp
Audience
Talon.One
Audience
Feed
Event
Loyalty Feed
Tapad
Audience
Tapjoy
Audience
Taplytics
Event
Taptica
Audience
Teak
Audience
The Trade Desk
Audience
Event
Cookie Sync
Ticketure
Feed
Triton Digital
Audience
TUNE
Event
Valid
Event
Vkontakte
Audience
Vungle
Audience
Webhook
Event
Webtrends
Event
White Label Loyalty
Event
Xandr
Audience
Cookie Sync
Wootric
Event
Yahoo (formerly Verizon Media)
Audience
Cookie Sync
Yotpo
Feed
YouAppi
Audience
Regal
Event
AWS Redshift (Define Your Own Schema)
The Redshift integration with Analytics is available for Enterprise customers only. If interested, please contact us. You are required to grant Redshift access to Analytics by creating a standalone VPC Security Group, attaching the Security Group to your Redshift Cluster, and creating a read-only Redshift account for Analytics to use.
If there are additional enrichments required, such as joining with user property tables or deriving custom user_ids, please contact us.
Instructions
In order to perform the following steps you must have administrative access to the AWS Console as well as your Redshift database.
Start In Analytics
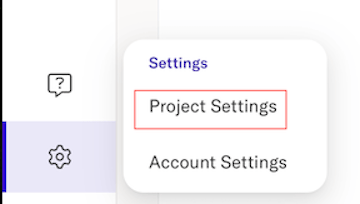
- In Analytics, click on the gear icon and select Project Settings.
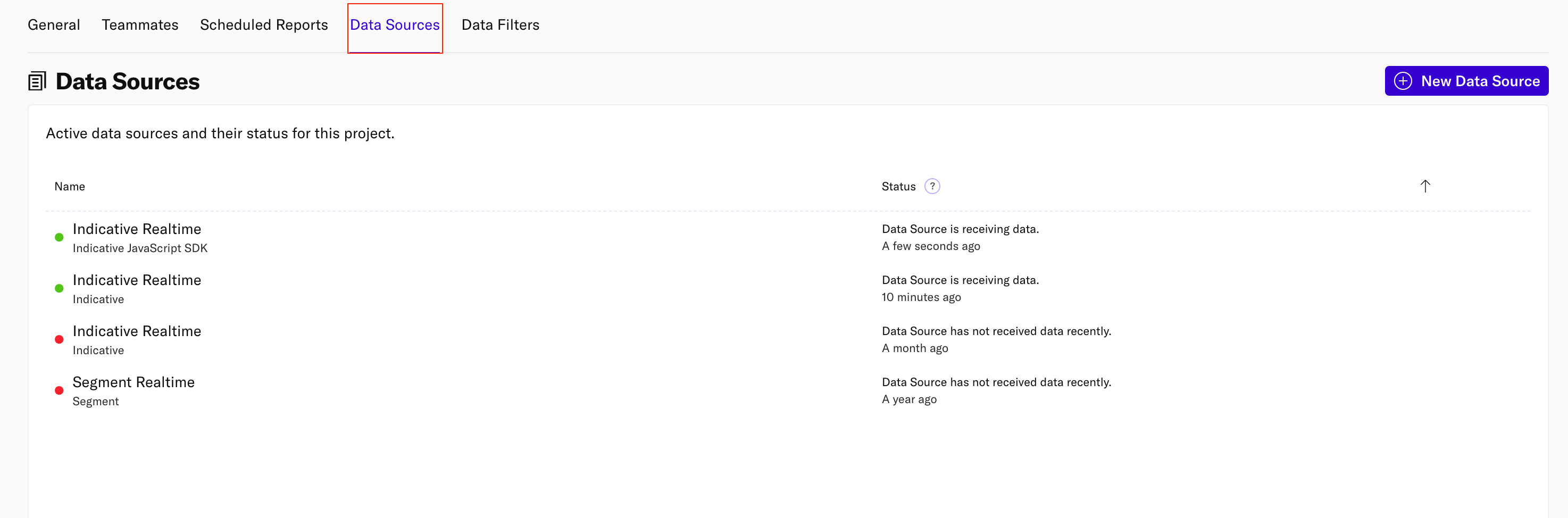
- Select the Data Sources tab.
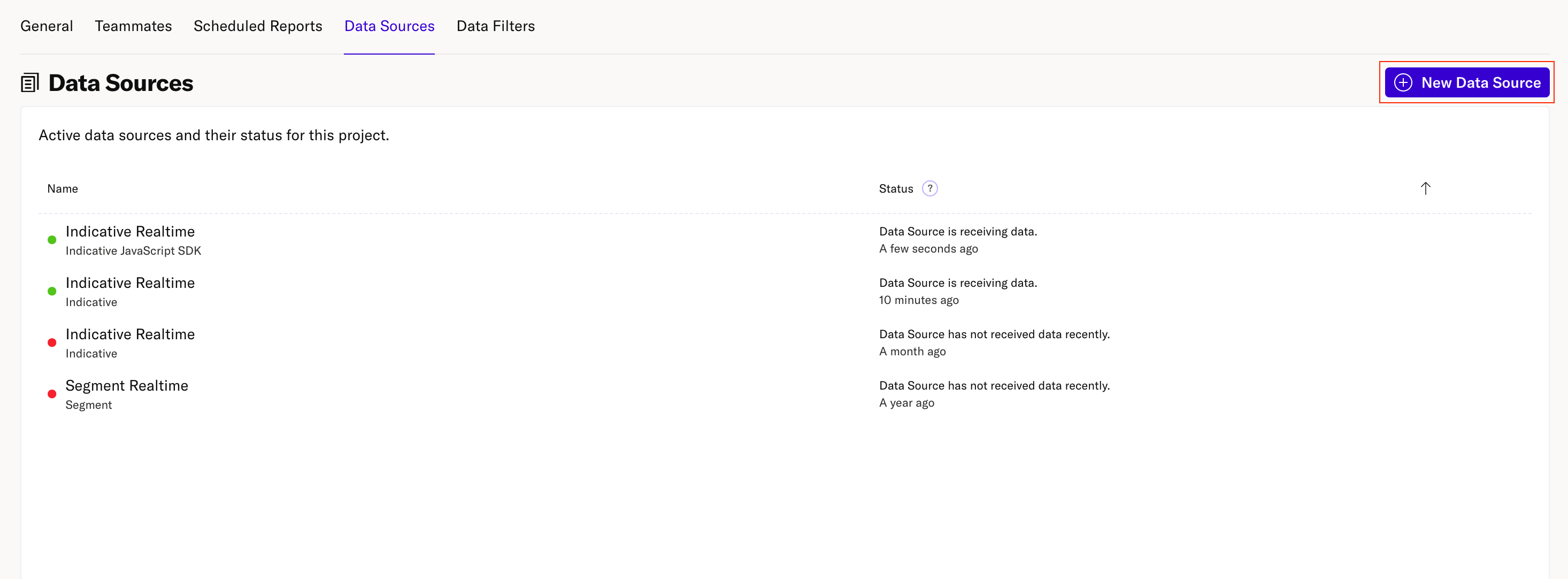
- Select New Data Source.
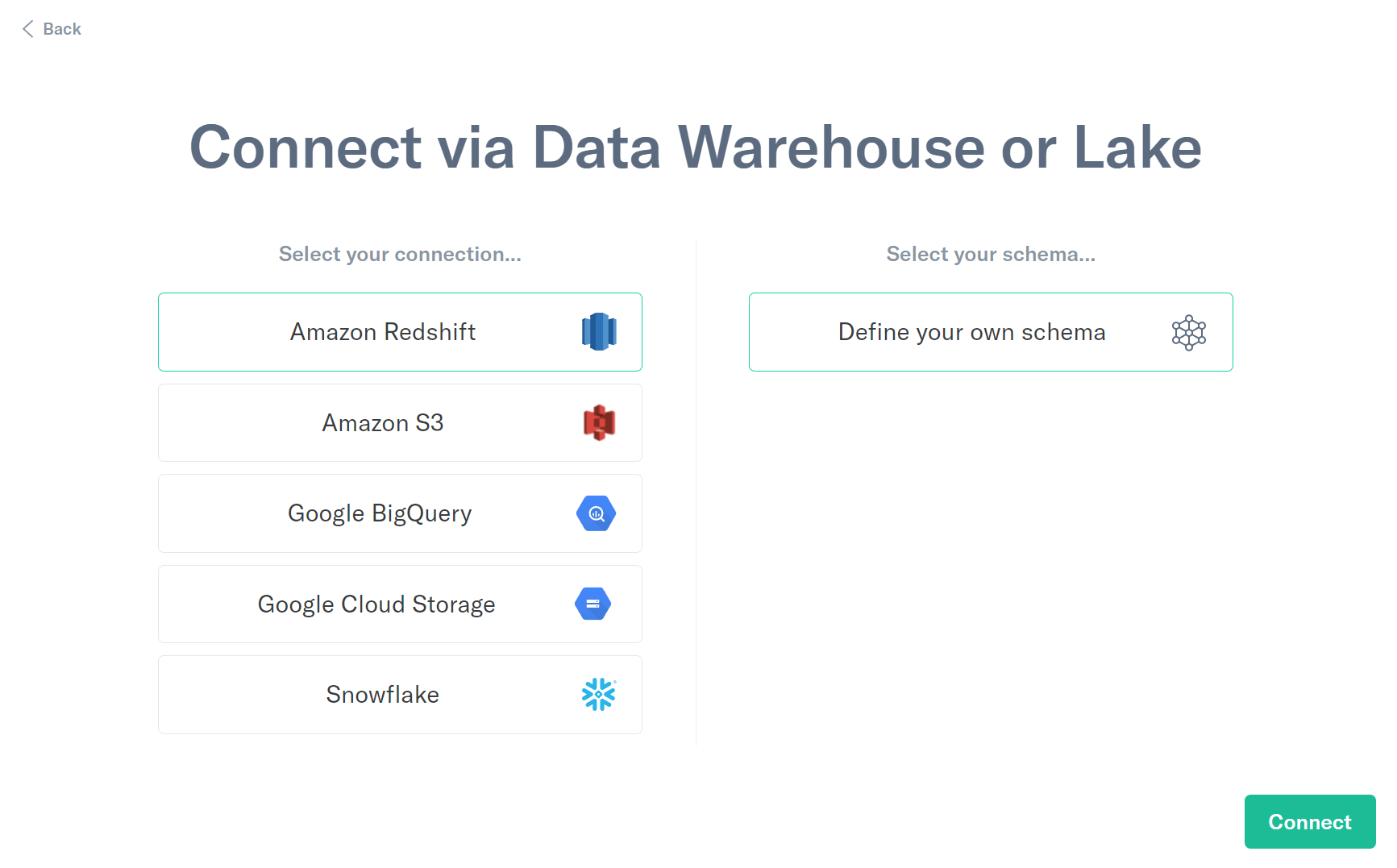
- Select Amazon Redshift and click Connect.
Connection Information
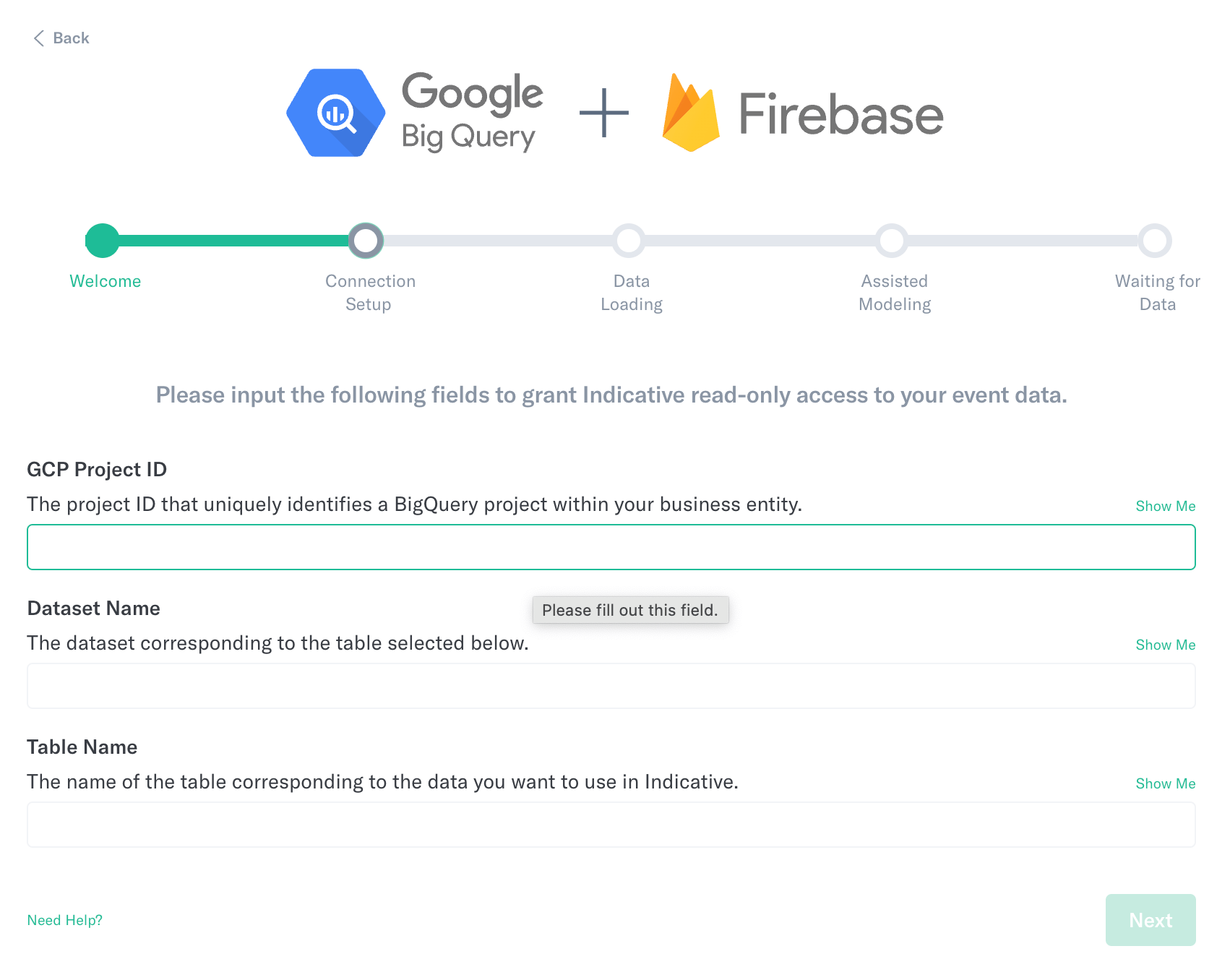
- The following fields can be found by accessing your AWS Console. Note: The Auto-Generated password is a password that Analytics has randomly generated. If you prefer to use your own password value, please replace the value in that field to your preferred password.
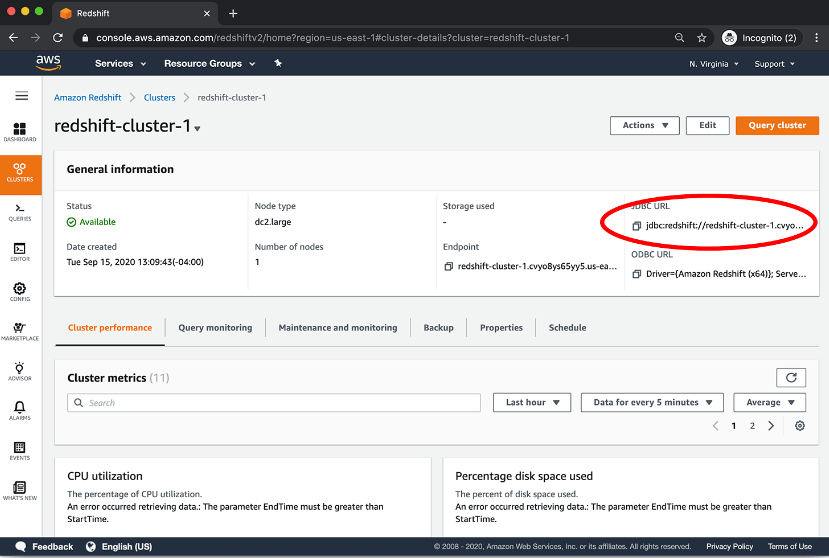
- Enter the Full JDBC URL by accessing your AWS console and selecting Clusters on the left side navigation. Click on the name of your Redshift Cluster to get this detailed view.
- Enter the Schema. Click here for additional information about schemas.
- Enter the Table Name that contains your event data.
- You can use the default Analytics Username, or choose to modify that to whatever fits your naming convention.
- Copy the Auto-Generated Password or create your own. This will be the Analytics user password that you will use later on.
- Click Next.
Create Security Group
The next step is to grant access to your Redshift cluster when accessed from Indicative’s IP addresses. This involves creating a new Security Group in your VPC.
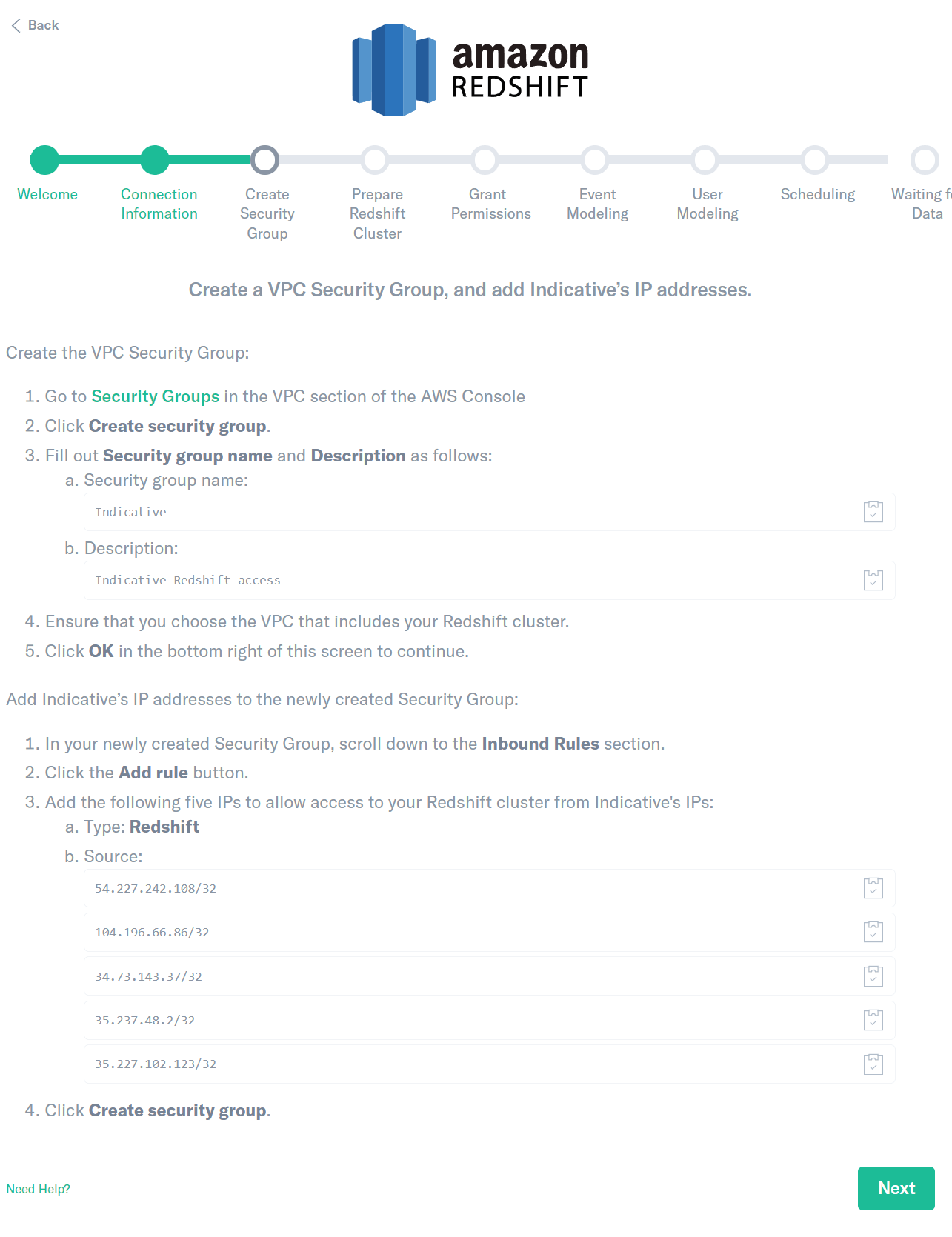
- Go to IAM Management in the Console and choose Roles from the sidebar.
- Click Security Groups on the left side.
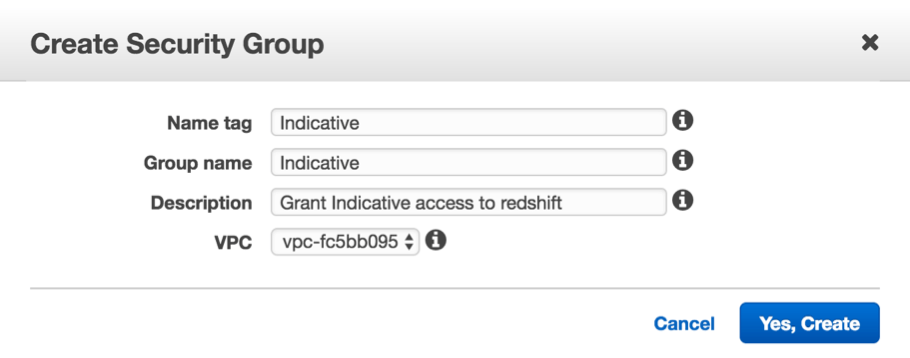
- Click Create Security Group.
- Fill out Name tag and copy the Group name and Description from Analytics. Make sure you choose the VPC that also includes your Redshift cluster. Click “Yes, Create” to continue. We recommend using the values below.
-
Add Analytics’ IP addresses to the newly created Security Group.
a. Select your newly created Security Group.
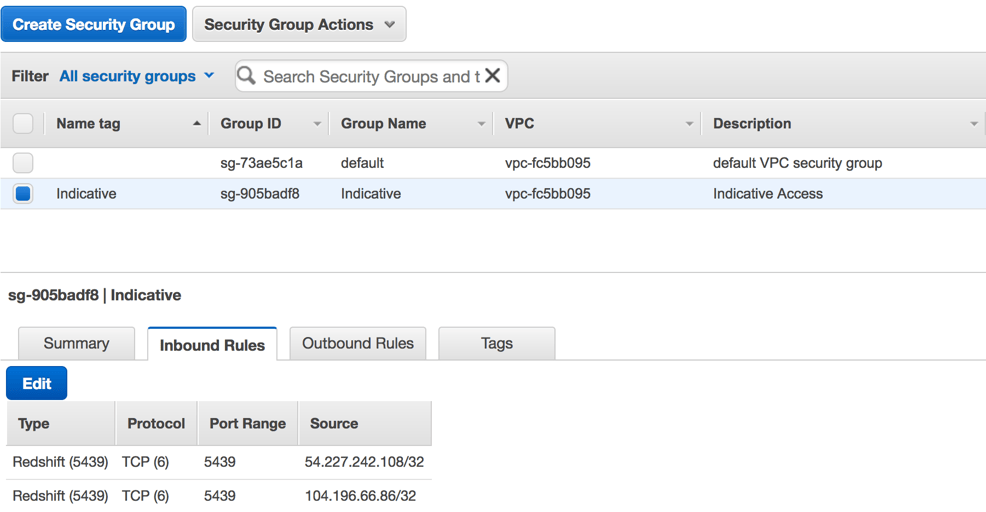
b. Click the Inbound Rules tab.
c. Click the Edit button.
d. Add the following three rules to allow access to your Redshift cluster to Analytics’ IPs:
- Type: Redshift; Source: 54.227.242.108/32 - Type: Redshift; Source: 104.196.66.86/32 - Type: Redshift; Source: 35.227.102.123/32 - Type: Redshift; Source: 35.227.125.106/32
Prepare Redshift Cluster
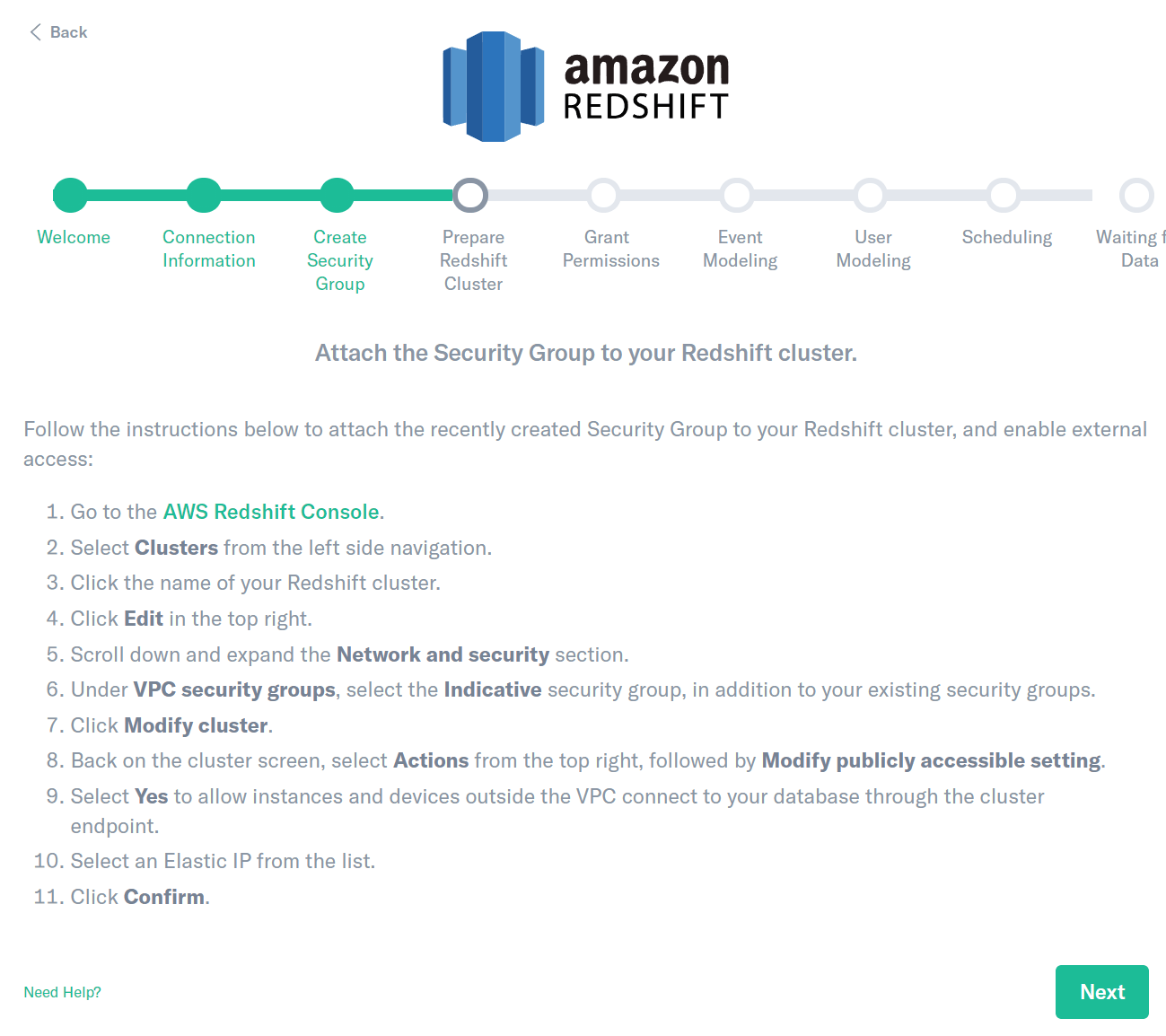
- Go to Redshift Console.
- Click the name of your Redshift cluster.
- Go to Cluster > Modify.
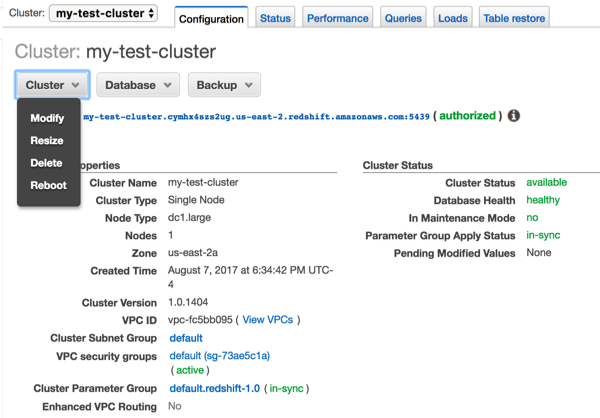
- Select the Indicative security group, in addition to your existing security groups.
- Set “Publicly accessible” to “Yes”.
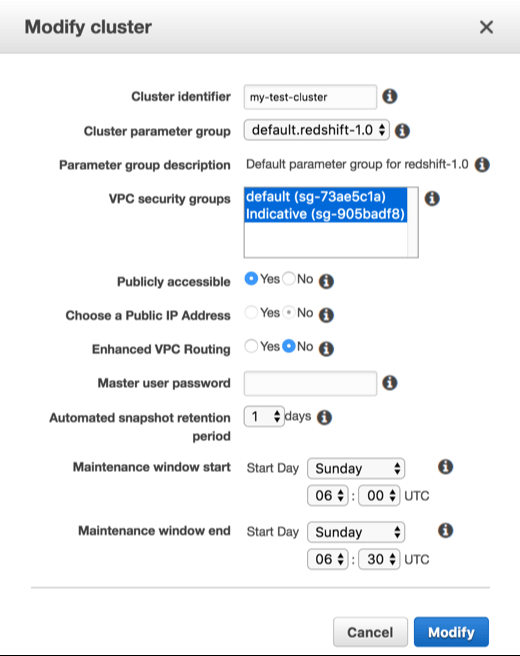
- Select an Elastic IP from the list.
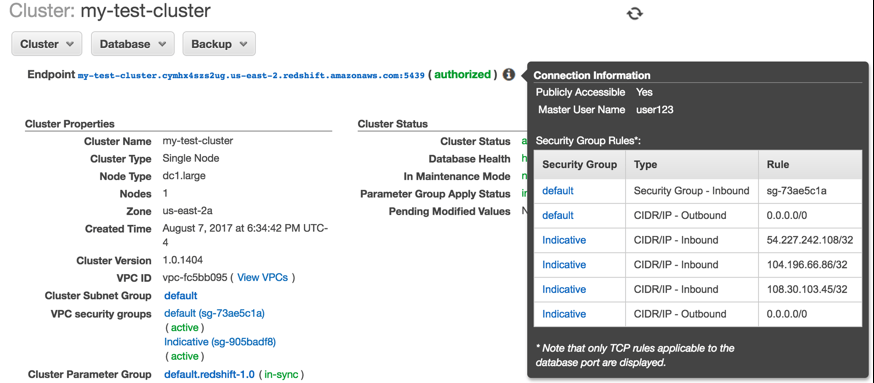
- When complete, your cluster status should look like this:
Grant Permissions
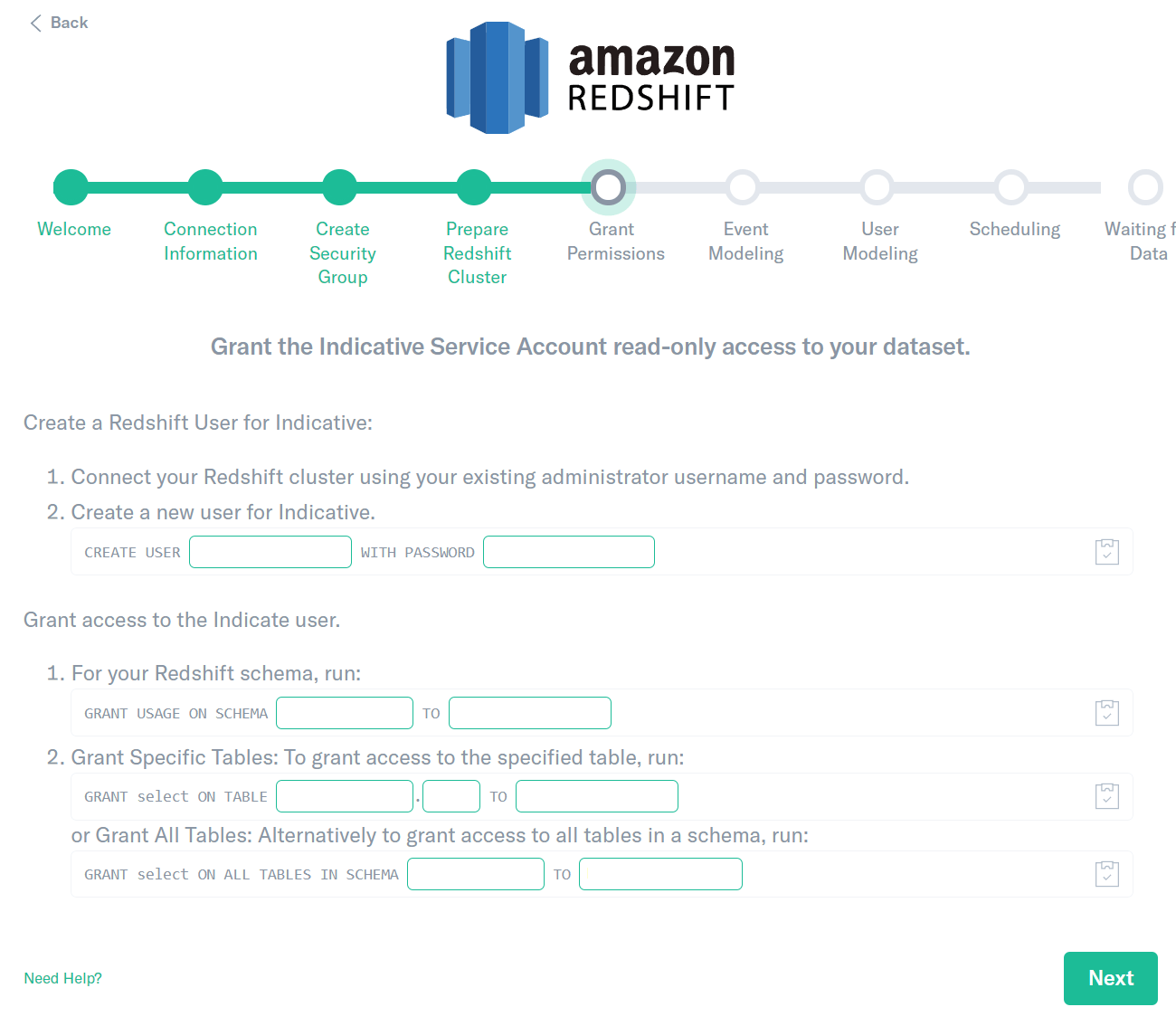
- Connect to your Redshift cluster using your existing administrator username and password.
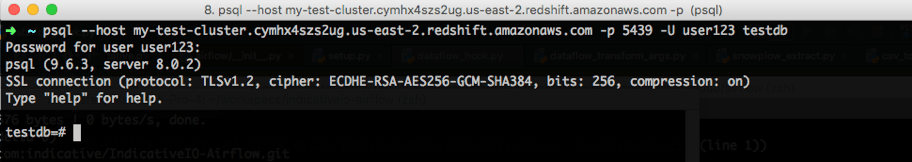
- Create a new user for Analytics. a. Copy the Create a new user for Analytics command from the Analytics screen and execute the SQL command.
- Grant access to the Analytics user. a. For your Redshift schema, copy the For your Redshift Schema command from Analytics and execute the SQL command. b. For the tables in your schema you’d like Analytics to access copy the Grant Specific Tables command from Analytics and execute the SQL command. c. Alternatively to grant access to all tables in a schema, copy the Grant All Tables command from Analytics and execute the SQL command.
Event Modeling
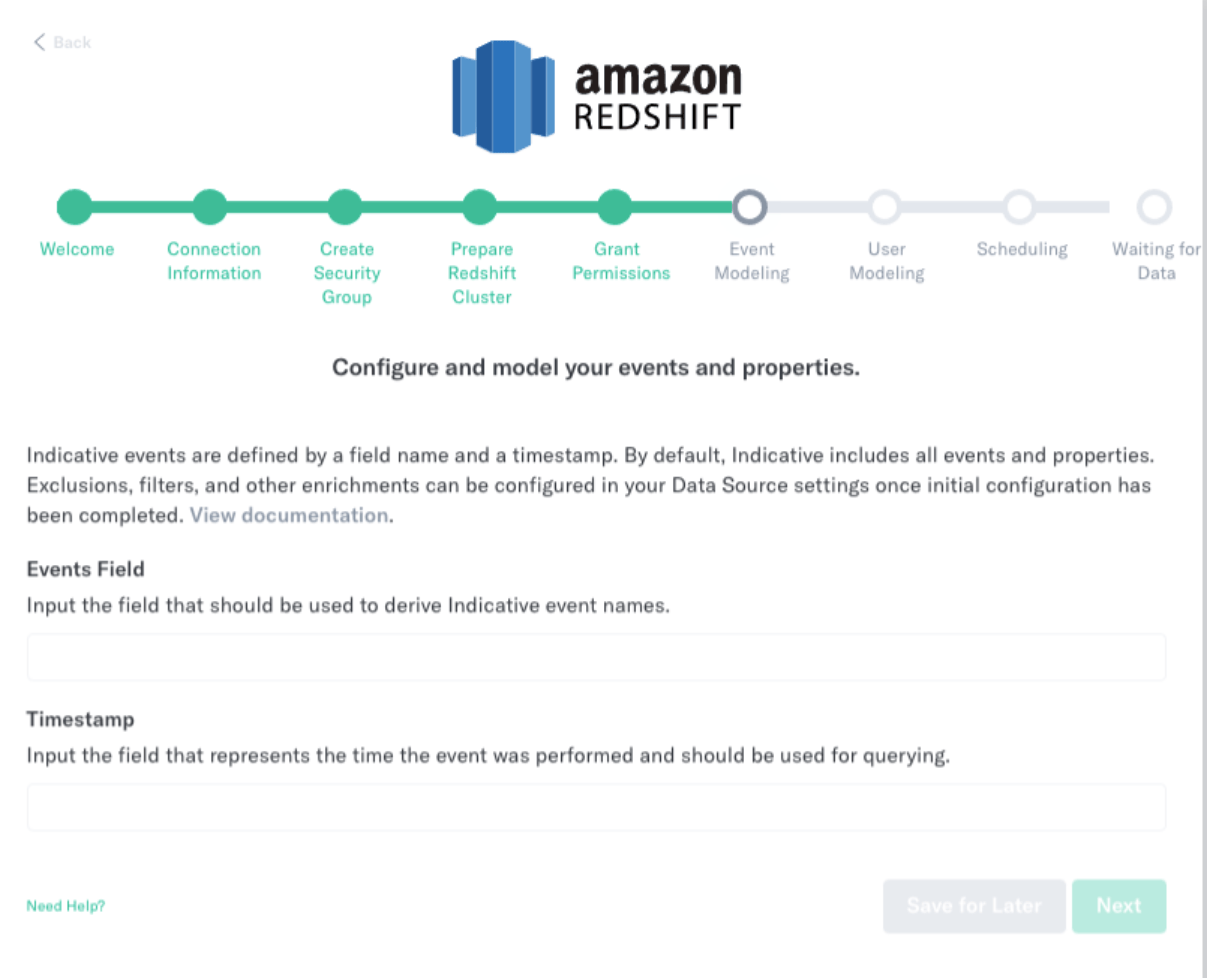
- Events Field - enter the name of the field that should be used to derive your Analytics event names.
- Timestamp - enter the name of the field that should be used for querying in Analytics.
- Click Next.
User Modeling
For more information on User Identification (Aliasing), please refer to this article.
- If you choose to enable Aliasing: a. Unauthenticated ID - Input the field used to identify anonymous users. b. Authenticated ID - Input the field used to identify known users.
- If you choose to disable Aliasing, press Disabled: a. Unauthenticated ID - Enter the field used to identify your users. All users must have a value for this field.
- Press Next.
Scheduling
- Select the Schedule Interval to adjust the frequency at which new data is available in Analytics.
- Set the Schedule Time for when the data should be extracted from your BigQuery environment. It is critical that 100% of the data is available by this time to avoid loading partial data.
- Select Save.
Waiting for Data
Once you see this screen, you’re all set! A Solutions Engineer will begin preparing your data, and you should be notified via email when ready.
Advanced Settings
For additional advanced settings such as excluding certain events and properties, please refer to this page.
If you have any questions or concerns about the above Integration, please contact your Customer Support Manager, or email support@mparticle.com.
Was this page helpful?
- Last Updated: March 3, 2026